How to detect a malicious email
Blog|by Leanne Bevan|18 October 2022
One of our leading cyber security vendors, Heimdal Security, has shared some key signs on how you can detect a malicious email. Take a look below.
Prevent a phishing attack by following these steps:
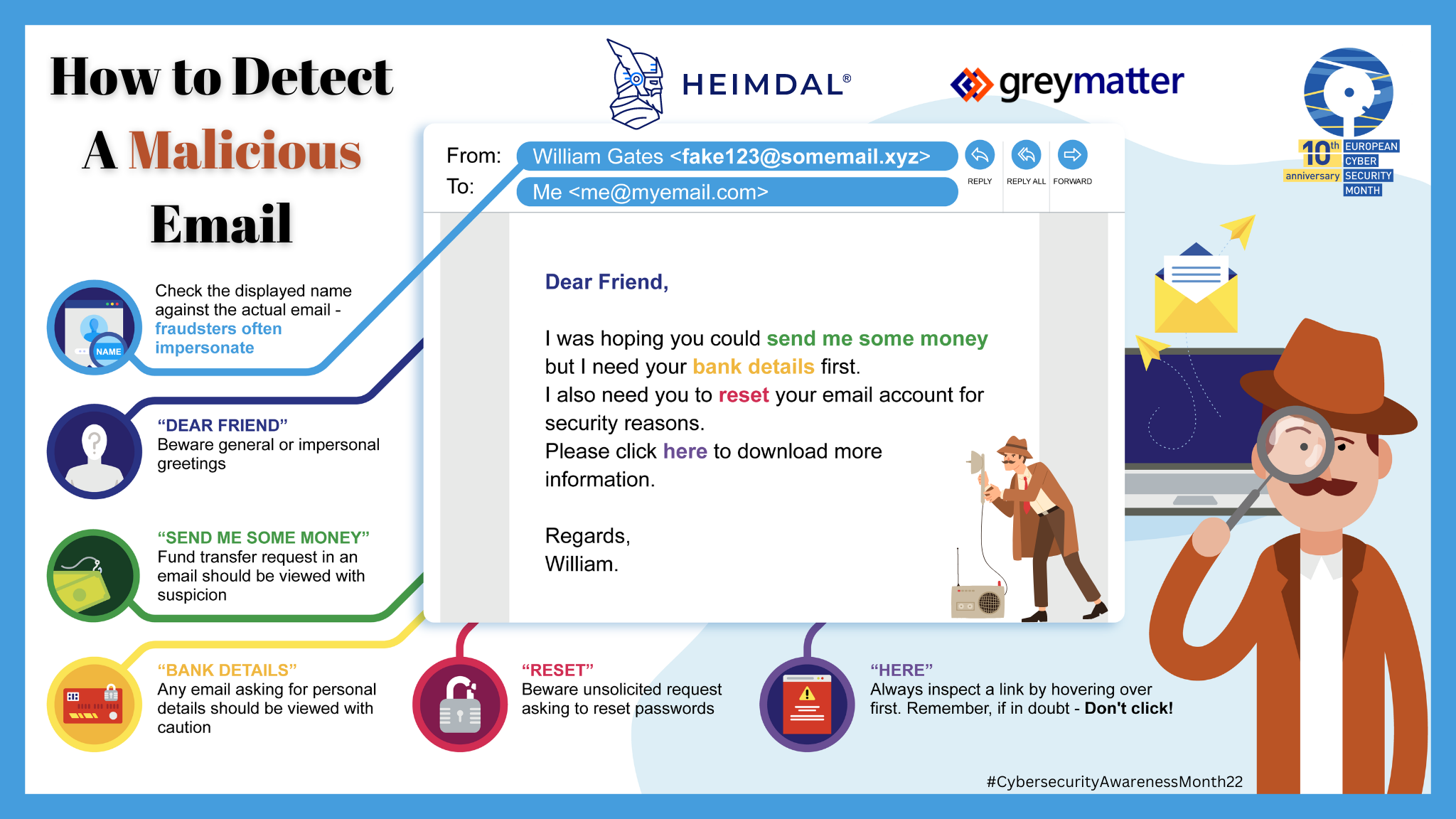
- Check the displayed name against the actual name - fraudsters often impersonate legitimate or fake people.
- Be aware of general or impersonal greetings such as "Dear Friend".
- Any email that asks for funds to be transferred should be viewed with suspicion.
- In addition, any email asking for personal details, such as bank details, should be viewed with caution.
- Beware of unsolicited password request emails.
- Always inspect a link by hovering over the link first. If in doubt, don't click it.
If you're still unsure, contact your IT department to check the email too.
Cyber Security Awareness Month
Preventing phishing and educating organisations and individuals on how to spot signs of it, is one of the focuses of Cyber Security Awareness Month.
Head to the page to find out more about how to prevent phishing, and the other areas you should look into to enhance data protection.
Get support from Grey Matter
Grey Matter is a Heimdal Security partner; we can provide licensing advice, quotes and trials.
Our cyber security expert can run through various threats in more detail, and all the solutions need to ensure multi-layered protection is in place.
Fill in the form below to book a consultation with our specialist.
Contact Grey Matter
If you have any questions or want some extra information, complete the form below and one of the team will be in touch ASAP. If you have a specific use case, please let us know and we'll help you find the right solution faster.
By submitting this form you are agreeing to our Privacy Policy and Website Terms of Use.
Leanne Bevan
Related News
Intel oneAPI 2024.1 A Milestone Release
What’s new in Intel oneAPI 2024.1 The 2024.1 release of Intel® Software Development Tools marks a major milestone for developers AND the entire software industry: the Intel® oneAPI DPC++/C++ Compiler has become the first compiler to fully support the SYCL...
ISV Partner Day Shortlisted for CRN Sales & Marketing Award
ISV Partner Day has been shortlisted for "Best Customer Event" at the CRN Sales & Marketing Awards
Microsoft 365 and Azure Security Tools: Microsoft Intune
In the second video in our series of short videos discussing Microsoft 365 and Azure security tools and concepts, our Microsoft experts cover off all you need to know about Microsoft Intune! Intune is a robust cloud-based solution to safeguard...
Women in Tech: A New Era | Roundtable
Fri 21 June 2024 5:00 pm - 11:30 pm BST
Get ready to shake it off (and network like nobody’s watching) because we’re hosting an exciting exclusive Women in Tech event with ESET that you won’t want to miss out on. Join us and share feedback, experiences and insights with...