How to protect and hide your Bing Maps key
Guides|by Clemens Schotte|6 April 2022
When using Bing Maps for Enterprise in your solution/application, you need a Basic Key (limited free trial) or an Enterprise key to use the services. For example, you would add a Bing Maps Key to the script URL loading the Bing Maps Web Control like this:
<script src="https://www.bing.com/api/maps/mapcontrol?callback=GetMap&key={your bing maps key}"></script> Protecting
The Bing Maps key is mainly used to determine the usage and allow access to Bing Maps features. To protect your Bing Maps key, so it can't be misused on other websites, there is an option in the Bing Maps Dev Center to protect your key. This security option allows you to specify a list of referrers (website URLs) and IP numbers who can use your key. When at least one referrer rule is active, any requests that omit a referrer and any requests from non-approved referrers will be blocked, preventing others from using your key for requests. You can have up to 300 referrer and IP security rules per key.
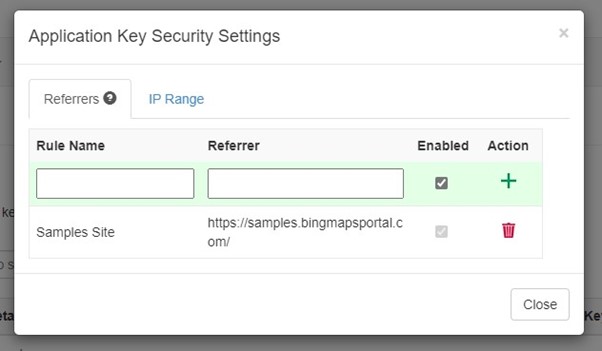
Your key is now protected but is still visible in your website code and it is best practice to never store any keys or certificates in source code. So how do you hide your Bing Maps key?
Hiding your Bing Maps key
To hide the Bing Maps key, you create a simple API endpoint that will only return the Bing Maps key if the request comes from a trusted referral URL. The Bing Maps Samples site is a good example that uses this approach.
In this example we are using an Azure Function written in C# that returns the Bing Maps key:
public static class GetBingMapsKey
{
private static readonly string[] allowd = { "https://samples.bingmapsportal.com/",
"http://localhost"};
[FunctionName("GetBingMapsKey")]
public static IActionResult Run([HttpTrigger(AuthorizationLevel.Anonymous, "get", Route = null)] HttpRequest req)
{
string referer = req.Headers["Referer"];
if (string.IsNullOrEmpty(referer))
return new UnauthorizedResult();
string result = Array.Find(allowd, site => referer.StartsWith(site, StringComparison.OrdinalIgnoreCase));
if (string.IsNullOrEmpty(result))
return new UnauthorizedResult();
// Get your Bing Maps key from https://www.bingmapsportal.com/
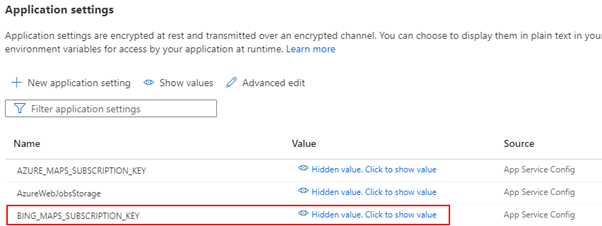
string key = Environment.GetEnvironmentVariable("BING_MAPS_SUBSCRIPTION_KEY");
return new OkObjectResult(key);
}
} The Bing Maps key is stored server-side in this Azure Function Application settings field. We are using the GetEnvironmentVariable() to get the key.
Next, we need to load the Bing Maps script and get the key from the API client-side. Finally, we use the following code snippet to load Bing Maps dynamically:
<script>
// Dynamic load the Bing Maps Key and Script
// Get your own Bing Maps key at https://www.microsoft.com/maps
(async () => {
let script = document.createElement("script");
let bingKey = await fetch("https://samples.azuremaps.com/api/GetBingMapsKey").then(r => r.text()).then(key => { return key });
script.setAttribute("src", `https://www.bing.com/api/maps/mapcontrol?callback=GetMap&key=${bingKey}`);
document.body.appendChild(script);
})();
</script> The browser will run this code and create at runtime in the DOM the same line of script tag we have seen at the beginning of this blog post to load Bing Maps and the Key. An additional advantage is that the Bing Maps key is not stored in the source code anymore and that you can use IaC and build pipelines to deploy the solution.
Tip: Only hiding the Bing Maps key alone is not enough as a security measure. We recommend you still enable the security option in the Bing Maps Dev Center!
If you have any questions about this post or want to know how to get the most from Bing Maps, please contact our Mapping team.
Tel: +44 (0) 1364 654 100
Email: [email protected]
Contact Grey Matter
If you have any questions or want some extra information, complete the form below and one of the team will be in touch ASAP. If you have a specific use case, please let us know and we'll help you find the right solution faster.
By submitting this form you are agreeing to our Privacy Policy and Website Terms of Use.
Author
Clemens Schotte
Senior Program Manager at Azure maps
Now a Senior Program Manager at Azure Maps as well as an AI and Developer Advocate and Cloud and Azure Strategist, Clemens has worked with Microsoft in various roles, starting as an Application Platform Consultant in 2007.
Related News
New changes to Visual Studio benefits: What you need to know
Microsoft is replacing legacy Visual Studio partner benefits with Visual Studio Enterprise Lite – and it’s going to change how your team access credits, licences, and tooling. What’s changing with Visual Studio Lite? From the introduction of Visual Studio Lite on 13 February 2026, you’ll no...
Strengthen your Microsoft Defender strategy with Sophos MDR
Cyber attackers aren’t slowing down – and they’re certainly not getting less sophisticated. Even with strong protections like Microsoft Defender in place, today’s human‑led attacks continue to slip through automated defences. That’s why more organisations are choosing to strengthen Microsoft...
The complete guide to the JetBrains AI ecosystem
AI is no longer a nice-to-have for development teams. It’s reshaping how you write, test and maintain code every day. JetBrains is one of the vendors pushing that shift furthest – and doing it directly inside the tools you already trust. JetBrains has evolved far beyond their productivity helpers like...
Azure Health Check: the five pillars that improve your cloud
Your Azure environment moves fast. Our Azure Health Check gives you a clear view of what’s working, what needs attention, and how to build a platform that’s secure, efficient, and ready to scale.